Author: Cord Oestmann
In a recent Oracle Ask Tom Database Backup and Recovery Office Hours presentation titled Ransomware Protection and Cyber-Resilient Architectures with Zero Data Loss Recovery Appliance, the Product Management team from Oracle provided a good introduction to the ever increasing features of the Recovery Appliance (RA) and how it provides for better cyber resilience of the platform. It came at an interesting moment as I not long ago had a conversation with a customer about the possible benefits of deploying the RA for their Oracle Database estate as a means to covering the organisation against ransomware attacks. The customer’s response was that he was looking at a generic solution that would protect all storage for his critical assets (including backups) against ransomware attacks.
Without naming the preferred platform; He listed key features such as storage network segregation, separation of duties, zero trust authentication and file immutability as being part of such a solution. The basic punchline was, especially for backups, “I don’t want to have a separate solution for my Oracle Databases.” I think it would be fair to describe this conversation as one that didn’t lead to a meeting of minds. But that got me thinking …
Back to the drawing board
I went back over the lines of argument put forward by the customer. Initially with a view to identify where I would find the hole in the reasoning. Perhaps where he had been wrong or misinformed in what he had represented as comprehensive ransomware and cyber-security features available in the generic storage solution.
To be fair, I did not get anywhere with that as everything that he had said and represented turned out to be factually correct and reasonable. Once written to the solution (assuming correct configuration and implementation of all the available security features), files were indeed immutable. A malicious actor could not alter them without physically damaging the storage devices with a hammer or strong magnet, and the recovery process would retrieve them as written. If you forgive me being self-ironic here, had the near-unthinkable happened and I had been actually wrong? Was the RA in fact not necessary when trying to achieve ransomware protection for your Oracle Database backups?

Author: Cord Oestmann
It was at this point that I realised that I had committed the cardinal error of not keeping in mind what makes the RA functionality unique when it comes to backing up and assuredly recovering your critical Oracle Databases. Namely the knowledge of the internal make-up of the Oracle Database structure. This process guarantees backing up only good blocks, discovering and repairing storage corruptions – and using only good blocks in restoration. Not to mention the ability to compress Oracle Database encrypted backup data.
The ransomware protection features that I was discussing with the customer are not the issue. The RA will now match anything that a generic storage solution protecting against ransomware attacks can offer – with arguably greater operational support for the Oracle Database. It is that the RA will protect the internal integrity of the backup and recovery objects in a way that no generic solution can. Oracle owns this intellectual property (IP) and does not share it with any third-party storage solution providers. Now, people will possibly argue that the integrity validation functionality could be achieved by digging into the Oracle Recovery Manager (RMAN) tools layer – but with a limited number of APIs available and no operational support – this would amount to a massively risky custom development undertaking without meaningful vendor support.
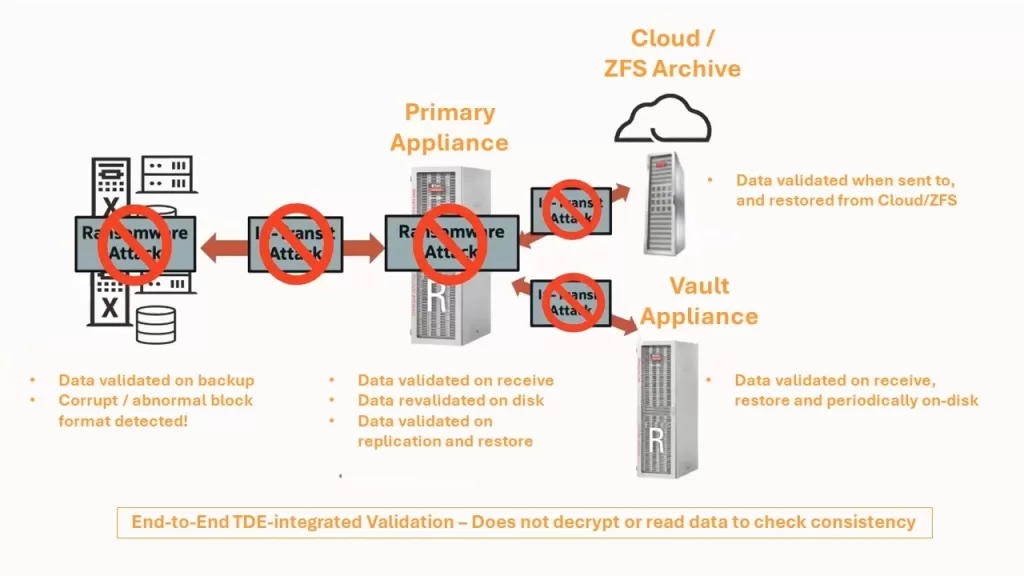
When all said and done – the question whether the RA is the appropriate solution for a customer comes down to answers to some key questions. The extent to which the considerations listed after the questions are reflective of the customer’s situation:
Things to consider:
- Is the value of the data held in your Oracle Databases sufficiently critical and/or valuable for you to be impacted if you were to lose it or it was exposed to unauthorised access? Does this value justify the cost of a ‘point’ solution?
Your regulator might be mandating you to take certain levels of precaution as part of compliance.
- How much does a generic backup solution-based Oracle Database backup and recovery strategy, including the integration into a ransomware attack and cyber-resilient storage solution, cost you for your Oracle Databases?
Do not neglect to include operational costs here. This effectively provides you with a simple comparator when looking at the cost of the RA as a solution. It is the solution that Oracle uses internally for its critical data and offers as the standard solution for critical data backup and recovery in its Public Cloud (OCI).
Things to consider:
- How much protection do you need to provide for your data held in your Oracle Databases at rest and in transit? i.e. Do you require it to be encrypted to be appropriately protected from malicious attacks?
While this will not materially affect the protection functionality of your generic storage solution, the use of encryption in the Oracle Database will mean that there is unlikely to be any storage compression in your backup and restore files.
- What is your Recovery Time Objective (RTO)?
For larger databases, or those generating high rates of change, a database restore can take many hours. Especially if the backup approach has been a combination of full and incremental backups. These would have to be assembled and cumulatively restored in order to arrive at the correct state of the data. Oracle Database encrypted, therefore uncompressed, data would be transmitted over the network, further impacting the recovery time. The RA only produces a single recovery backup set (the virtual full) and is capable of compressing Oracle Database encrypted data.
Recovery Point Objective
Crucially, what is your Recovery Point Objective (RPO) following an attack affecting data held in your Oracle Databases? The RA supports recovery up to the last successfully committed Oracle Database transaction due to its ability to take the real-time redo stream from the source Oracle Database. A generic solution only recovers data successfully backed up before an attack. Potentially leaving several hours to a day of data loss. This also assumes no one manipulated your backups during the process, which a generic backup solution cannot detect (relevant to the previous question as well).

Clarity
To be clear, the size of your Oracle Database estate, the criticality and associated business value of the data held in them – will play an important role in your decision making process. The RA is a comprehensive backup and recovery solution specifically designed for the Oracle Database with deployment options that provide a high degree of cyber resilience and protection against ransomware attacks, which is reflected in its cost.
However, if your Oracle Database estate is of a sufficient size and your requirements in this space match those outlined in this piece, I suspect you will find time spent assessing the solution well worth your while. Going back to the beginning, I am certainly planning on reopening the discussion with my customer on the subject, if for no other reason to ensure that he has a fuller understanding of the opportunity represented by the RA solution to address not just backup and recovery but also the built-in cyber resilience and ransomware protection for his Oracle Databases.
Interested to know more?
If these thoughts and observations have pricked your interest and you would like to better understand how Oracle Recovery Appliance can help to shape your Oracle Database backup and recovery. As well as improve your operational resilience and cyber security posture, Contact Us.
Contact us today to arrange an assessment or email:

Cord Oestmann
Principal Solution Architect at Vertice




